All about hashing

In today's digital world, data security is a major concern for individuals and organizations. From password protection to data integrity, it is essential to have robust mechanisms in place to ensure the confidentiality and authenticity of sensitive information. This is where hashing comes in.
Hashing, a fundamental cryptographic technique, offers a powerful solution to irreversibly secure the data.
In this article, we'll dive into the details of hashing, exploring how it works, its applications, and its relevance in the IT security landscape.

Get 200% Bonus after your first deposit. Use this promo code: argent2035
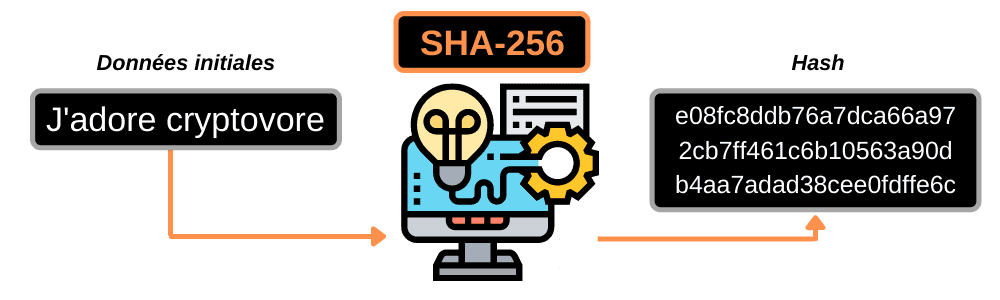
🚀 What is hash?
Hash, in simple terms, is a mathematical transformation that takes variable-sized data and converts it into a unique fixed-sized digital fingerprint. This imprint, often called “hash“, is a cryptographic digest that summarizes all the data of irreversible origin.
In other words, it is virtually impossible to reconstruct the original data from the hash, making hashing an essential one-way technique for ensuring confidentiality and information integrity.
One of the most common uses of hashing is data integrity checks. By calculating the fingerprint of a file or a set of data, it becomes possible to detect any alteration or modification of the data.
Even a minor change in the original data will result in a completely different fingerprint, making it easy to identify errors or attempted manipulations quickly.
The hash also finds its place in the field of cryptography, offering a strong password protection and sensitive information. Rather than storing passwords directly in a database, secure systems hash them before storing them.
When the user enters their password, it is again hashed and compared to the stored value for verification. Thus, even in the event of unauthorized access to the database, the passwords remain indecipherable.
However, not all hashing algorithms are created equal. Some are considered obsolete or vulnerable to advanced cryptographic attacks.
Security experts recommend the use of robust and well-established algorithms, such as SHA-256 or SHA-512, to ensure optimal security.
🚀Why the hash?
It is important to use the hash to be able to secure the transactions that have already been carried out and also those to come.
Once a modification is made on the network, you will absolutely have to modify all the previous blocks as well as their associated hashes. If we make a modification on the whole network, the hash which will be generated will be of yours.
Article to read: All about warrant
You will have to compare your hash as well as that of the network in order not to validate a transaction.
Indeed, the hash is one of the essential elements for the constitution of a Markel tree. It is therefore possible for certain cryptocurrencies to combine several hash functions which have different properties from the others.
🚀The rules and properties of hashing
For a hash function to be correct, it must follow certain rules and properties:
- The length of the signature used must always be the same no matter how much data you have entered. Later, we will see what are the lengths of the fingerprints in the hash functions.
- From fingerprints, it is impossible to find the original data: the functions in the hash only work in one direction.
- It is not possible to predict a signature. It is impossible for you to try to imagine the signature by examining the data.
- If you have multiple data, each data must have different signatures.
🚀How hashing works
In reality, hashing is an automated process that has the potential to be likened to the codes that are sent out during war.
In theory, it is simply necessary to add, shift, or transform the different characters of a message in order to obtain a code which must be completely different from the others and unique in its kind.
Article to read: Get crowdfunding for your project
The hash allows you to generate from a variable complementary input, a fixed code. Even if the length of the string is more than 5 letters or even 500 words, it still should only return a result with a single size.
Hash functions all contain the same properties. Which are :
- Determinist : directly, after the passage through the grinder of the function in question, the result of the message, in all circumstances, must be invariable: places, moment, repetition, …
- La resistance : the result obtained from the function must not allow anyone at any time to go back to the initial message.
- Separate : the result obtained from the function concerning two similar messages must not be similar but rather different and easily identifiable.
- Only : after analysis, two different messages cannot come out with the same result.
- Efficient : the result must not be delayed, it must be immediate.
The interest of hashing is therefore to standardize the contents to have an identical number of characters and to be able to identify the data in a unique way for one message to another.
🚀Practical use of different hash functions
This list is not complete at all, as there are several other uses of these functions:
- The comparison between passwords : as said, when saving your password, everything is done for security.
- Verification of your downloaded data : in some cases for example, when you download a file from the internet, the original signature of the file is available.
It is either directly displayed on the site or in another file which is separate. To reassure you that the file is correctly downloaded, you will simply have to check that the signature of the file is indeed the same with that provided.
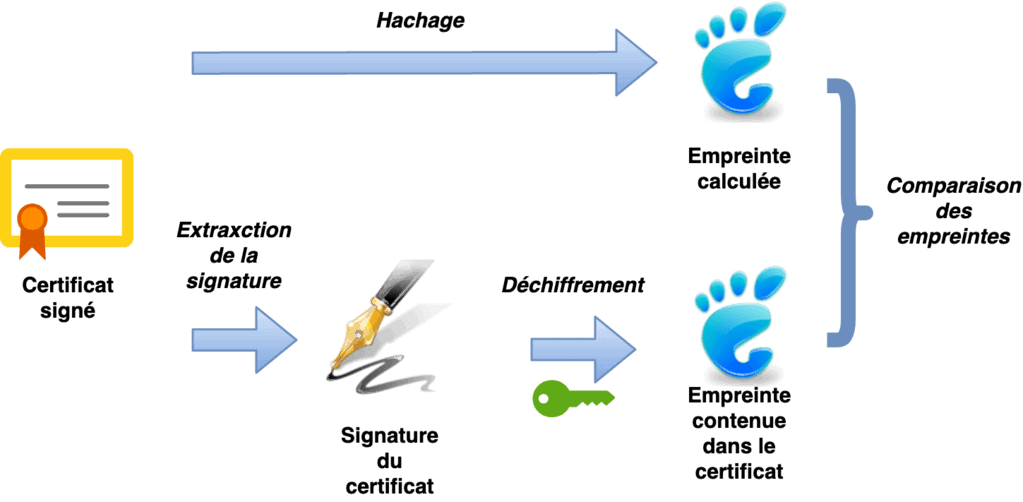
- Digital or electronic signature of documentss: here, the documents are sent directly to a hash function. The documents are sent at the same time as the fingerprints. The user would only have to decipher the fingerprint received and verify that it corresponds to the computation of the fingerprint attached to the data received.
- Use of hash table : if you want to do it, you will have to use it in software development to make everything go well.
- Regarding data storage : to reassure you of the presence of the document, you will have to reassure yourself that the signature is also there, so you do not need to save it again. This is very appreciated, because if it is a file which is large, it will take you much less time for the calculation of the signature of the registered fingerprint to be done.
🚀Using hash coding
The feature that keeps your passwords secure is the one that takes the text of your password and grinds it into a signature. This signature is also called footprint ».
The computer does not send your password to a server, it only transmits your password signature. At this time, the server does not save the password, but rather the signature that has been grinded.
Article to read: How to bet on Live TV Games on 1xbet

Get 200% Bonus after your first deposit. Use this official Promo code: argent2035
When the computer connects, the server will not verify the identity of your password, but rather whether the signature of your password is the same with the one registered.
So don't worry about anyone using your password, because the hash function reduces the risk of traffic with password grinding.
🚀Famous hash functions
Now we will introduce some famous functions and some sites that help you.
⚡️MD5
Surely some people have already heard of it. This hash function is very well used and more so in terms of security, it is advisable to switch to the most robust version available, because the consequences of collisions are present.
Article to read: Manage your business accounts well
Note that this function directly returns a 128-bit hash.
⚡️SHA1
SHA1 was formerly the replacement function of the MD5, because it sent 160-bit hashes and it gave no chance of encountering collisions.
This changed from 2004-2005, when several attacks showed the possibilities of generating collisions.
Since that date, it is not really advisable to use this function of SHA1. But today, many people still use this function.
As of December 31, 2016, digital certificates that used SHA1 are no longer valid.
⚡️SHA2
Consist of SHA256 et SHA512, they are the two largest standards that are currently in use.
We say this with certainty, because we have not yet found any security vulnerabilities on these different functions. They have the possibility of producing signatures in height respectively of 256 and 512 bits.
Finally, we are going to introduce you to some sites that give you the possibility of generating digital signatures with files or data, and also using different hash functions.
- If you want to encrypt a text, you have: http//www.cryptage-md5.com/
- To encrypt in English: http://onlinemd5.com/
Be sure to use them well to take advantage of their functions.
🚀Conclusion
The hash is more than just a mathematical function. It is a powerful tool in the field of computer security. In this article, we explored the fundamentals of hashing and its relevance in today's digital landscape.
We have learned that hashing provides an effective method for verifying data integrity, detecting tampering or errors. Moreover, it plays a vital role in securing passwords, making them unbreakable and thus protecting sensitive information.
Article to read: How to finance your project on a tight budget?
Beyond these common uses, we also discovered the multiple applications of hashing in various fields of computing. Whether for data storage, deduplication, hash tables or information retrieval, hashing proves to be a versatile and effective tool.
However, it is crucial to choose the hashing algorithm carefully according to the specific needs. current standards, such as SHA-256 or SHA-512, provide higher levels of security and should be preferred over outdated or vulnerable algorithms.
Frequently Asked Questions
⚡️What do we use a hash for?
The interesting thing in the hash is in no way the data in question, but rather their signatures which allow a good level of data security.
⚡️What is a hash collision?
A collision is represented when several different data from each other give the same fingerprint. But don't worry if this happens, because it's only a matter of making a simple check if the fingerprint that we received for the data is the same with that of the data sent.
We finished !!
We hope you were satisfied and that hash functions have no more secrets for you.

















Leave comments